Currently, any business, regardless of its size or market niche, is present on the network. The digital economy has led us to establish a new front to protect ourselves from cybersecurity threats. Therefore, we want to tell you what you should do against them today. Keep reading to find answers to your questions.
The main cybersecurity threats:
The security of the company continues to be a crucial point. It has been for the past decade and will continue to be for years to come. Hence, we invite you to take note of the main cybersecurity threats forecast for this year:
- Data leak: It involves unauthorized access to confidential data or sensitive information resulting in the release of this information into an untrusted environment.
- Deepfake technology: They are manipulated images or videos to make users believe that they see a certain person through statements or actions that never happened.
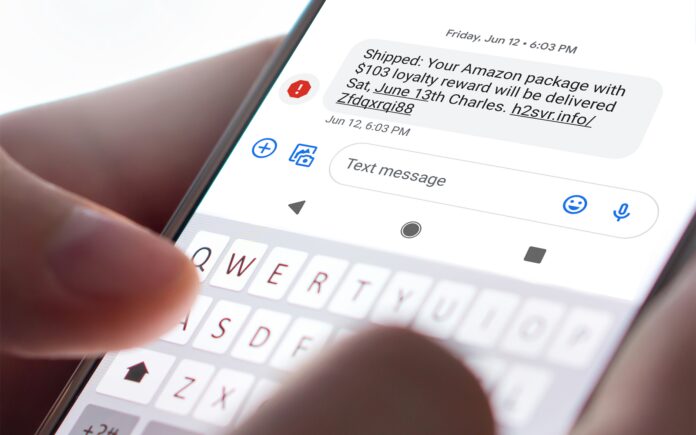
- Smishing: This technique consists of sending an SMS or email by a cybercriminal posing as a legitimate entity.
- Human factor: Lack of cybersecurity awareness among employees leads to many mistakes being made that cause, propagate, or enable a security breach.
- Attacks on the supply chain: This type of threat is mainly targeted at partners or third-party vendors of the company whose computer network was attacked by hackers.
That’s not all. In addition, there are other web vulnerabilities that you should be aware of:
Loss of access control:
Allows a user without permission to access a company resource, which may lead to the disclosure of sensitive information.

Faulty security settings:
The lack of configuration or the presence of obsolete versions with vulnerabilities without updating leave a door open to unauthorized access to our systems.
Identification and authentication failures:
When the access interface is not controlled correctly, we run the risk of identification and authentication failures. This can lead to brute force or dictionary attacks (with a cyber-criminal going through all possible variants to guess our password, including a ‘dictionary list’ of common phrases used by individuals and organizations).
Failures in security monitoring:
The lack of records in the event logs means that incidents or offenders cannot be detected. The log records all errors, informational messages, and program warnings. Regular review of the event log history reveals the security holes, which is especially important for servers.

Vulnerable and outdated components:
Known vulnerabilities in common components, such as the version of the operating system, can compromise the system or application. In some cases, the impact may be small, but in others, it can lead to large security breaches.
10 things to do against cybersecurity threats:
Do you know that most cyber-attacks can be prevented? As they are becoming more common, it is important to know what to do to protect yourself and your company. Several measures can be taken to reduce the risk of becoming a victim of a cyber-attack:
1. Update software and operating systems. You should keep your software and operating systems up to date, as the latest versions always include security enhancements.
2. Use strong passwords. It is essential to use strong passwords, which are not easy to guess. You should use a combination of letters, numbers, and special characters, or even better, a good Identity, Access, and Password Management System.

3. Keep devices secure. It is crucial to keep devices secure, as if they are infected with malware, they can be used to carry out cyber-attacks. We recommend installing an antivirus on all devices connected to the internet, as this helps protect them against threats.
4. Do not open unsolicited messages. Never open unsolicited emails, SMS, or other messages because they may contain malware, such as viruses, spyware, ransomware, etc. As for texters, you can check their identity by their phone number on PhoneHistory and make sure he/she is a genuine person.
5. Do not visit unsafe websites. Avoid visiting unsafe websites, they could be a gateway to malicious programs.
6. Respond promptly and quickly to incidents. Businesses need to respond quickly to cybersecurity incidents to protect their employees, customers, and assets. According to the Verizon Cybersecurity Report, 66% of businesses take more than a day to respond to a cybersecurity incident.
For this reason, disaster recovery services are increasingly implemented in companies. They ensure the preservation of business activity of the organization in emergency situations and concern the restoration of information and system performance in the event of a disaster.
7. Raise awareness and train employees. Cybersecurity training is essential to reduce cyberattacks caused by human error. It may be a course, but its effects on employees fade over time. There are annual awareness services that allow awareness to always be kept in mind since people are always the weakest link.

8. Make a security copy. All company data must have a backup copy that allows its recovery.
9. Carry out cybersecurity audits regularly. It is important to detect possible vulnerabilities in your infrastructure and the best way to do it is through a systematic cybersecurity audit.
10. If you do not have time or resources to dedicate to cybersecurity, think about hiring a SOC Service, where cybersecurity professionals will ensure that your company is protected.
Year after year, companies should strengthen their systems and applications in the fight against cybersecurity threats. Keeping the workplace safe is vital to guarantee a suitable environment.
But cybersecurity is sometimes a jumble of juxtaposed dynamics. Competition between IT departments and cost-conscious companies means that it’s often not the best system that is running, but rather the one that is within the company’s budget.
Criminals also walk the path of least resistance, hoping that someone just isn’t paying attention to that weird email that has slipped through spam filters and asks an employee to update their account information. Financial institutions are looking for greater integration and interconnection, but that also means that any outage in the system has a greater impact.

In addition, stronger controls for businesses and customers accessing online systems and services means higher costs and possibly longer delays in gaining access to information, which could upset multiple account holders.
But despite all this, in an age of increasing cyber threats, businesses know they need to harden systems and encourage employees to be more cautious and security aware.





